The U.S. is exploring the idea to establish cybersecurity labels on IoT devices and software, in hopes it will both inform consumers of risks and motivate manufacturers to improve the security for the flood of new products entering the market.
Internet-of-Things (IoT) devices number in the billions, some estimates are as high as 46 billion, and continue to emerge at a quickening pace with consumers and across industrial uses. Yet they often are weak when it comes to being hacked, which creates growing risks to consumers’ privacy, security, and even safety.
The U.S. has indicated a desire to adopt some kind of labeling and has kicked off discussions with manufacturers. The National Institute of Standards and Technology (NIST), within the U.S. Dept of Commerce, is leading the effort and is soliciting input from IoT manufacturers and the public.
Given the self-interest involved, I am somewhat skeptical of what the manufacturing industry will recommend or voluntarily implement when it comes to Cybersecurity Labels for IoT devices. The core problem is that the industry itself is not putting forth the effort to implement basic cybersecurity functionality into its product architecture and designs. This group is now being asked to develop a label standard to help consumers and I expect the results to be less than stellar.
On the upside, I do applaud the creative concept of security labeling as an out-of-the-box idea and involving the private sector, but this path has significant weaknesses when it comes to how the relevant content of the disclosures will be decided and the challenges for meaningful absorption by the consumer.
There are many efforts, by security, overseas governments, and academic organizations, which show promise but also have challenges.
The CyLabs team out of Carnegie Mellon University has developed a very comprehensive label, but I think it is far too complex for consumers to understand.
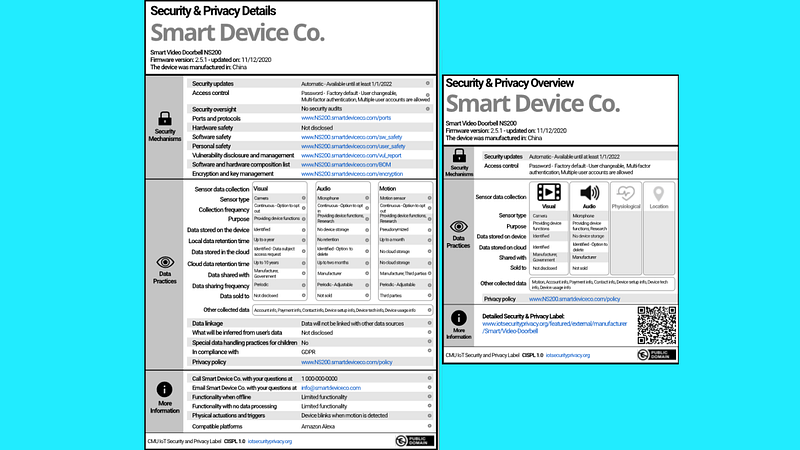
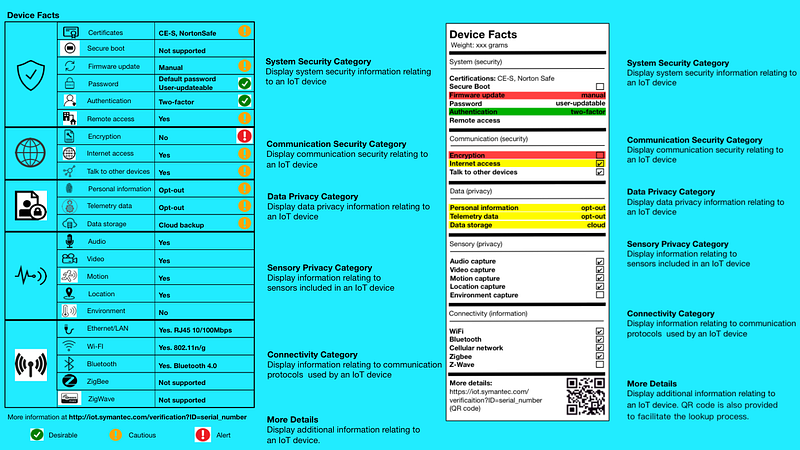
Symantec has developed a scaled-down version of what CyLabs proposes, but the data does not readily translate to something meaningful to the average consumer.
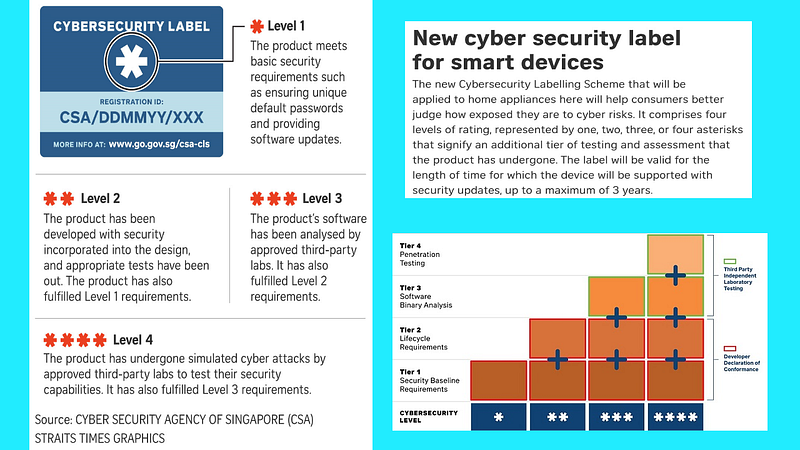
The city-state of Singapore strikes a balance between independent verification and self-reporting, but overall, it is overly simplistic to convey a meaningful risk picture.
I would rather the government foster the development of an independent rating scale that gives simple scores for compliance to basic hardening configurations, resistance to compromise, exposure risk to other systems, privacy, and trust of the vendor’s ethics consistency.
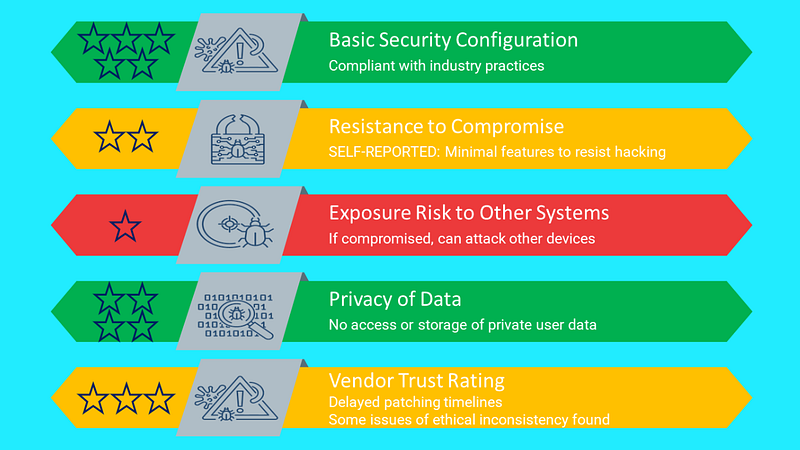
Combined with allowances to support the economics of manufacturers self-reporting, but with limited scores and only for some of the categories. An approved independent body would be required for the ratings of some categories and access to higher scores. Finally, the results must be presented in simple icons for consumers with perhaps some plain English that highlights the result
For comprehensiveness, labeling should be made a requirement to encourage competitiveness by vendors to deliver meaningful security for IoT products.
Label information must also be clear and meaningful to convey the risks to consumers. To make sure the ratings are consistent and not manipulated, independent verification will occur at a minimum in some areas, such as vendor trust, and for any area where a rating is higher than average.
I also caution letting the IoT manufacturing industry take the lead for any type of labeling, we risk either very complex labels, which won’t be comprehended by consumers, or overly simplistic labels that barely scratch the aspects necessary to understand the relevance of the security posture for the device or software.
IoT devices are easily compromised and then either used against the owner or are herded into botnets that can attack other systems on the Internet. Cybercriminals and hackers realize that the vast number of unsecured IoT devices is an excellent resource to leverage in pursuit of their goals.
If we are going to go down this path of security labeling, we must do it correctly for it to become a catalyst of enhanced security for these products.
A rational system must be proposed, where clear goals are defined which benefit consumers. Otherwise, it is a wasted effort and an unfortunate delay in addressing the systemic problem of IoT security.

Comments