We had a community webinar on "XDR : A Holistic View Through Security Analytics – Across Endpoint, Network And Cloud". We discussed the fundamentals; Endpoint solutions vs XDR; Implementation experience, challenges; post implementation feedback, outcome vs expectation, use cases; MDR vs human skills.
Session Agenda
- What is EDR, XDR
- Endpoint solutions vs XDR
- Implementation experience , challenges
- Post implementation feedback, outcome vs expectation, use cases
- MDR vs human skills
About Speaker
- Abdur Rafi, Head IT Infrastructure & CISO, ABP Group
- Soumya Biswas, IT Infrastructure & Security Specialist, ABP Group
- Debajyoti Das, Senior Executive IT Security, ABP Group
(Webinar) Recorded
Discussion Highlights
1. Extended Detection and Response (XDR) solutions are designed to provide automated threat detection and response through data visibility and the use of threat intelligence and data analytics. XDR collects activity data from multiple vectors including endpoints, servers, and networks.
2. Automobile Attack Surfaces : Fifteen of the most hacable and exposed attack surfaces, including several electronic control units on a next generation car. Like - Smartphone, Remote link type app, Airbag ECU, OBD2, USB, Bluetooth, DSRC-Based Receiver (V2X), Remote key, Passive keyless entry, Vehicle access system ECU, Steering and Braking ECU, Engine and Transmission ECU, Lighting system ECU, ADAS system, TPMS
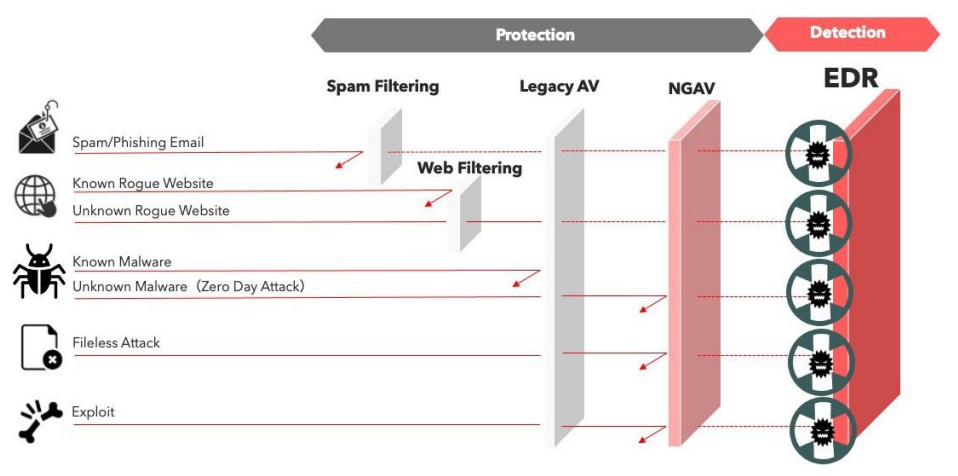
3. Endpoint Detection & Response
- Spam Phishing email
- Known Rogue eebsite
- Unknown Rogue website
- Known Malware
- Unknown Malware
- Fileless Attack
- Exploit
4. Endpoint Protection Plan (EPP)
Detection : Ioc scan, Advanced detection techniques, Behaviour analysis
Investigation : Root cause, Attack Visualization, Enriched alert data
Response : Automated response on discovery, Multiple response options, Quick response during the investigation
5. How XDR works : XDR isolates and dissects threats on different attack surfaces
- Endpoints
- Network
- Servers
- Cloud workloads
6. Endpoint Protection Policies
- Threat Protection
- Peripheral control
- Application control
- Data Loss Prevention
- Web Control
- Update Management
- Windows Firewall
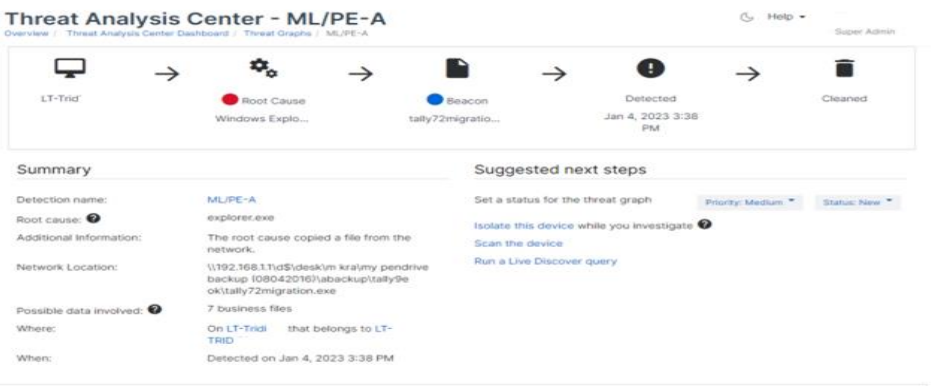
7. Threat Analysis Center - ML / PE-A

Comments