Topic Brief
We already talked about developing a modern security operations center or a SOC and some of you were left with questions how do you actually journey ? how do you travel to this modern SOC ? It's easy to discuss what the modern SOC should be but how do we get there ? In my writing and speaking some of the links i mentioned on the slide here i've covered this topic but I wanted to present a condensed version of some highlights of how to actually grow your SOC to achieve that type of a modern framework
About Speaker
Dr. Anton Chuvakin is presently the Security Advisor at Office of the CISO, Google Cloud. He is a computer security specialist, and until recently was a Research Director at Gartner for Technical Professionals (GTP) Security and Risk Management Strategies (SRMS) team. Formerly he was also a principal at Security Warrior Consulting. Previous positions included roles of a Director of PCI Compliance Solutions at Qualys. , a Chief Logging Evangelist with LogLogic, a U.S. Log Management and Intelligence company and a Security Strategist with netForensics, a U.S. Security information management company. He is an author of many publications and invited talks on computer and network security and a co-author of "Security Warrior", "PCI Compliance", "Logging and Log Management: The Authoritative Guide to Understanding the Concepts Surrounding Logging and Log Management.
About CISO Platform
CISO Platform is an exclusive community for senior security leaders with 40,000+ professionals globally
It's been 10 years since we started ciso platform community with the vision of collaboration and learning among senior security executives. We thank all our members for promoting knowledge and making the online world safer together. The community today has grown over forty thousand plus subscribers globally. Our primary goal has been to create tangible community goods and as a community we have created more than 1000 checklists frameworks and security training material that are available absolutely free for all. We have also conducted 50 plus training sessions for school kids as part of the kids cyber safety initiative. We would encourage you to write blogs and articles and also establish yourself as a thought leader in our community at www cisoplatform.com
We invite all security heads to the community. Help us reach out to more security peers like you. If you know a peer or friend who might be a security professional, do invite him to sign up at www cisoplatform.com Memberships are free for security professionals
Keynote (Recorded)
Session Summary :
Motivators for improving SOC is more business change, not just threat change. Threats keep changing but businesses become more digital, agile. The challenge is to deal with ransomware on cloud, mainframe, PC, server. So the stack of IT changing and business change is very competitive. This is a great reason to dramatically changing SOC rather than a gradual improvement.
Digital Transformation = Attack Surface Expansion ?
• Users work from everywhere using different types of apps and devices
• Users are of many kinds : employees, partners, contractors….
• Users have higher expectations, and attacks are becoming more targeted and sophisticated
SOC is a team. You can buy the technology but you can always get the right people. The mission of SOC is to detect incidents and properly dealt with.
Why are we changing the SOC ? Forces that push SOC – 1.Expanding attack surface. 2.Security talent shortage. 3.Too many alerts from too many tools. Prevention has limits. So, we end up focusing on detection and response.
Improve SOC 10% or 10X ?
The 10X philosophy. The notion of “10x thinking” is at the heart of how we innovate at Google. To put the idea simply: true innovation happens when you try to improve something by 10 times rather than by 10%.
It’s often easier to make something 10 times better than it is to make it 10 percent better. You’re working to make things 10 percent better, you inevitably focus on the existing tools and assumptions, and on building on top of an existing solution that many people have already spent a lot of time thinking about. Such incremental progress is driven by extra effort, extra money, and extra resources. But when you aim for a 10x gain, you lean instead on bravery and creativity. Humans can let go of resource constraints and achieve great results with the 10X challenge
We need to transform SOC 10X not just improve.
Traditional SOC :
• Inspired by IT helpdesk philosophy
• Treats incidents as rare and abnormal
• Focuses on alert pipeline, and pairs alerts to analysts
• Centered on SIEM (SOC = SIEM Analyst Team)
• Has walls between alert handles and alert tuners
• Threat intelligence is sometimes consumed
• Shallow metrics on handling time
Modern SOC :
• Teams are organized by skills not rigid level
• Process structures around threats not alerts
• Threat hunting covers cases where alerts never appear
• Multiple visibility approaches not just logs
• Automation via SOAR works as a force multiplier
• Deeper testing and coverage analysis
• Threat intelligence is consumed and created
• SOC elegantly uses third-party services
Possible ways to create 10X SOC ?
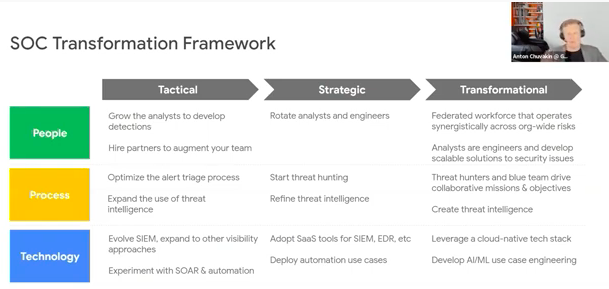
1.SOC Transformation Framework
This is inspired by how modern companies operate like Google, Netflix. This is how future SOC needs to work to keep up
Bucket 1 : People Transformation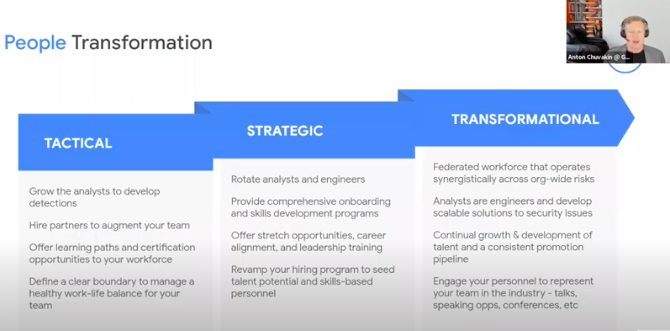
Tactical• Grow the analysts to develop detection
• Hire partners to augment your team
• Offer learning paths and certification opportunities to your workforce
• Define a clear boundary to manager healthy work life balance for your team
Strategic
• Transformational
• Rotate analysts and engineers
• Provide comprehensive on boarding and skills development programs
• Offered stretch opportunities, career alignment and leadership training
• Revamp your hiding program to see the talent potential and skills based personnel
Transformational
• Federated workforce that operates synergistically across org-wide risks
• Analysts are engineers and develop scalable solutions to security issues
• Continual growth and development of talent and a consistent promotion pipeline
• Engage your personnel to represent your team in the industry – talks, speaking opportunities, conferences, etc.
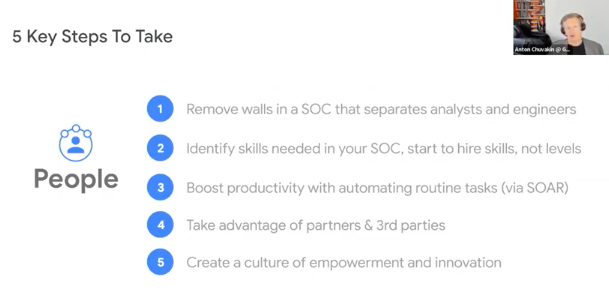
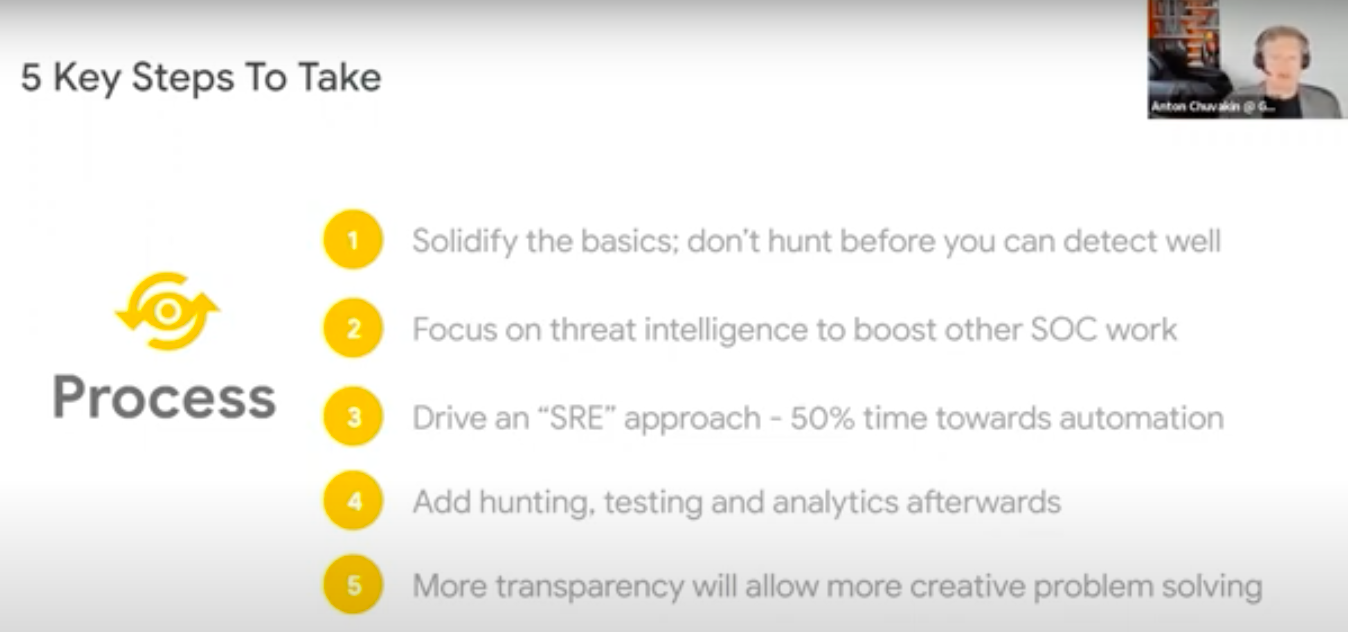
5 Key Steps To Take
• Remove walls in a SOC that separates analysts and engineers
• Identify skills needed in yourself, start to hire skills, not levels
• Boost productivity with automating routine tasks (via SOAR)
• Take advantage of partners and third parties
• Create a culture of empowerment and innovation
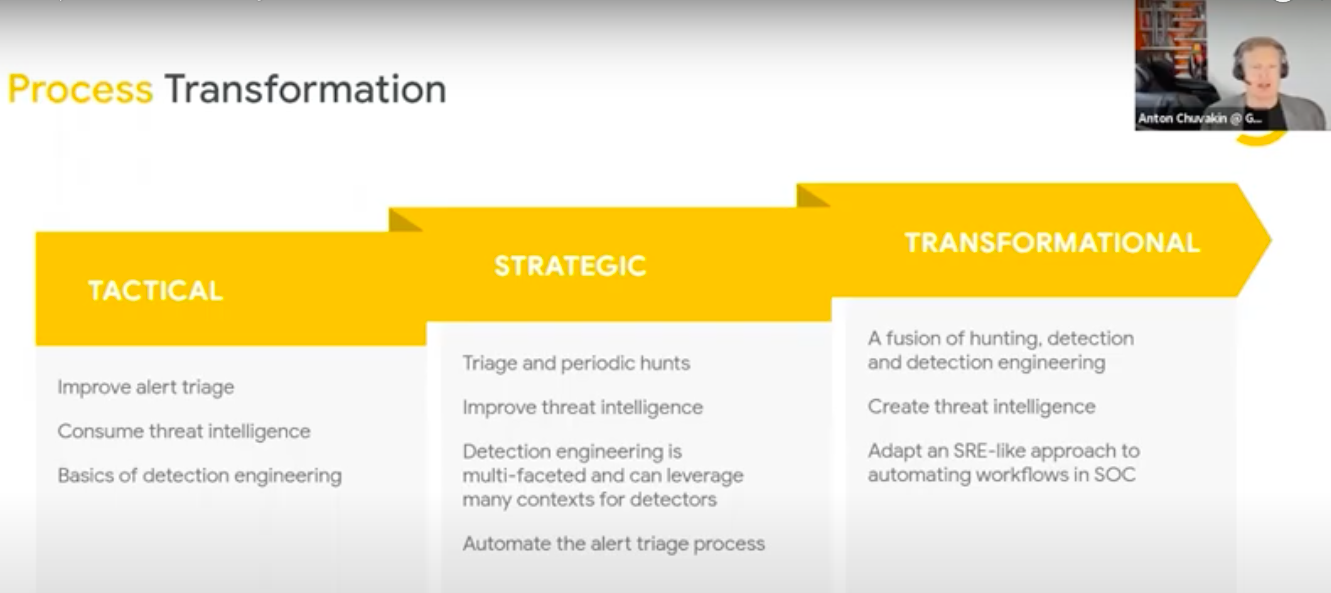
Bucket 2 : Process Transformation
Tactical
• Improve alert triage
• Consume threat intelligence
• Basics of detecting engineering
Strategic
• Triage and periodic hunts
• Improve threat intelligence
• Detection engineering is multi-faceted and can leverage many contexts for detectors
• Automate the alert triage process
Transformational
• A fusion of hunting, detection and detection engineering
• Create threat intelligence
• Adapt an SRF-like approach to automating workflows in SOC
5 Steps To Take
• Solidify the basics; don’t hunt before you can detect well
• Focus on threat intelligence to boost other SOC work
• Drive an “SRE” approach – 50% time towards automation
• Add hunting, testing and analytics afterwards
• More transparency will allow more creative problem solving
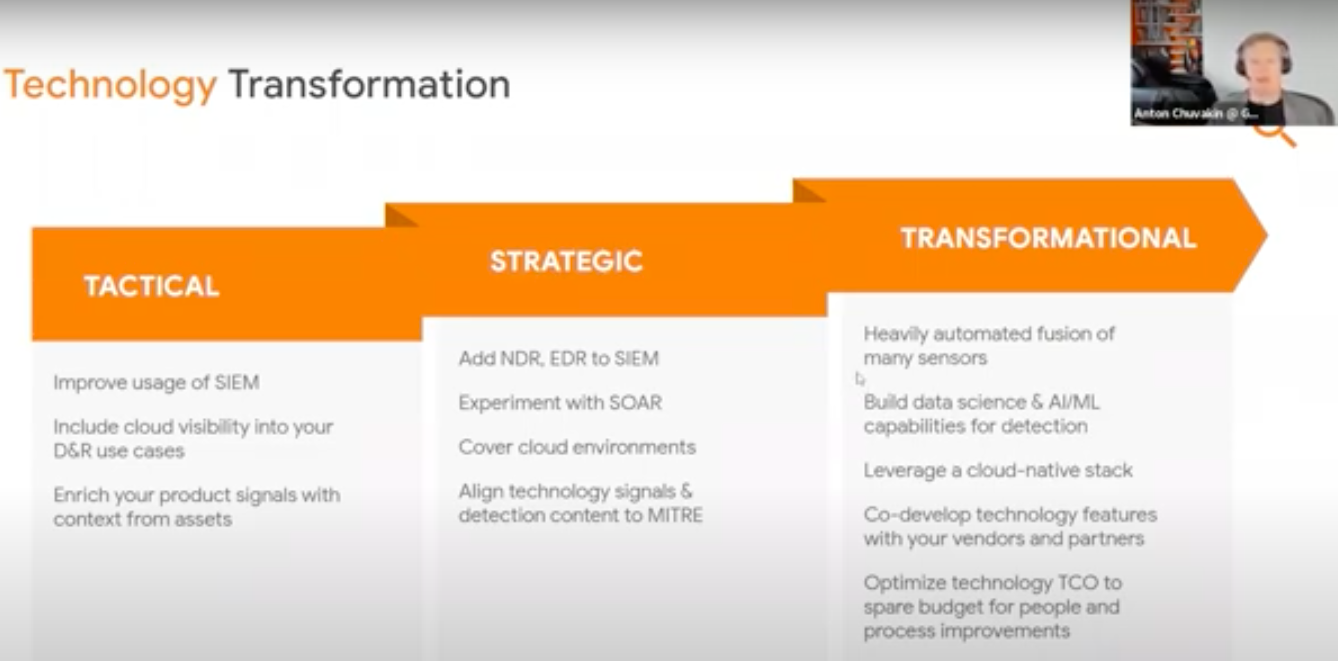
Bucket 3 : Technology Transformation
Tactical
• Improve usage of SIEM
• Include cloud visibility into your D&R use cases
• Enrich your product signals with context from assets
Strategic
• Add NDR, EDR to SIEM
• Experiment with SOAR
• Cover cloud environments
• Align technology signals & detection content to MITRE
Transformational
• Heavily automated fusion of many sensors
• Build data science & AI/ML capabilities for detection
• Leverage a cloud-native stack
• Co-develop technology features with your vendors and partners
• Optimize technology TCO to spare budget for people and process improvements
5 Key Steps To Take
• Don’t discuss a SIEM / UEBA
• Expand visibility : NDR, EDR (XDR?), cloud etc.
• Be aware that SaaS tools will win in the end
• Use SOAR to automate
• Use ML but don’t assume magic
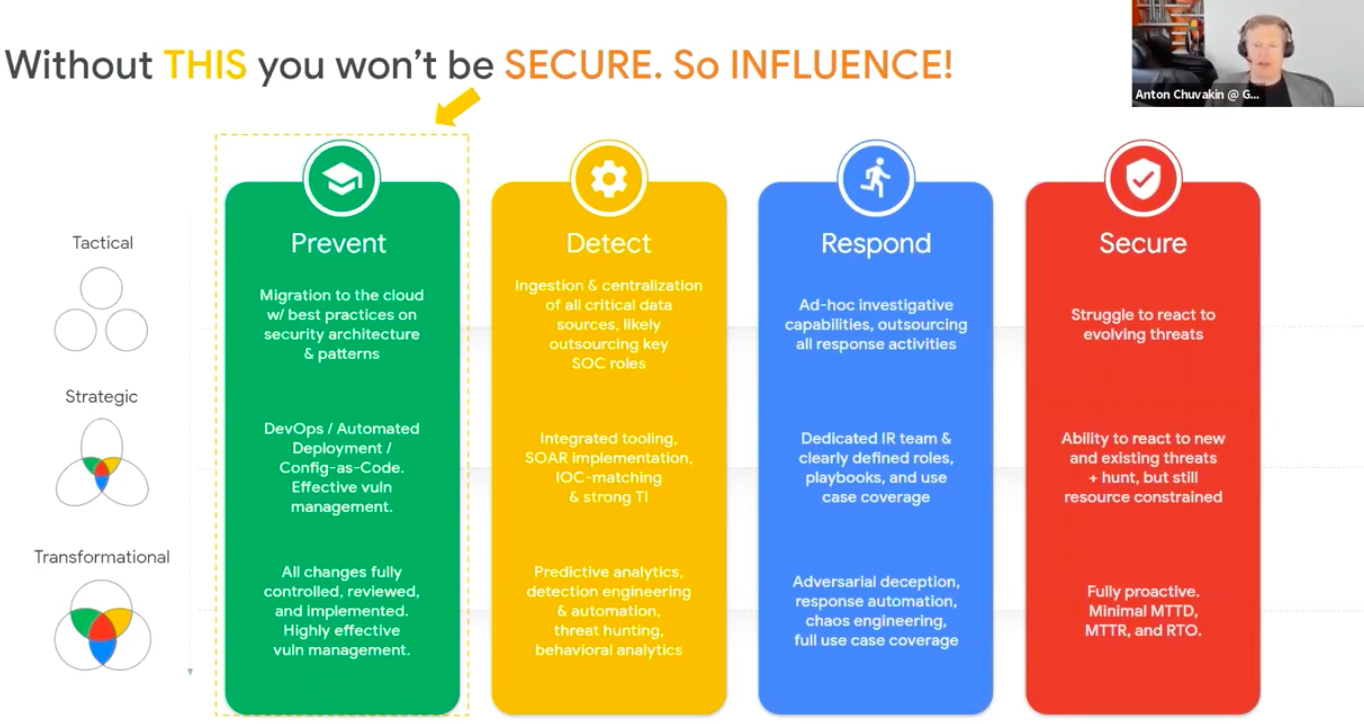
Without THIS you won’t be SECURE.
Prevent
• Migration to the cloud with best practices on security architecture & patterns
• DevOps / Automated / Deployment / Config-as-code. Effective vulnerability management
• All changes fully controlled, reviewed and implemented. Highly effective vulnerability management
Detect
• Ingestion and centralization of all critical data sources, likely outsourcing key SOC roles
• Integrated tooling, SOAR Implementation, IOC – matching & strong TI
• Predictive analytics, detection engineering & automation, threat hunting, behavioural analytics
Respond
Ad-hoc investigative capabilities, outsourcing all response activities
Dedicated IR team & clearly defined roles, playbooks, and use case coverage
Adversarial deception, response automation, chaos engineering, full use case coverage
Secure
• Struggle to react to evolving threats
• Ability to react to new and existing threats + hunt but still resource constrained
• Fully protective. Minimal MTTD, MTTR and RTO
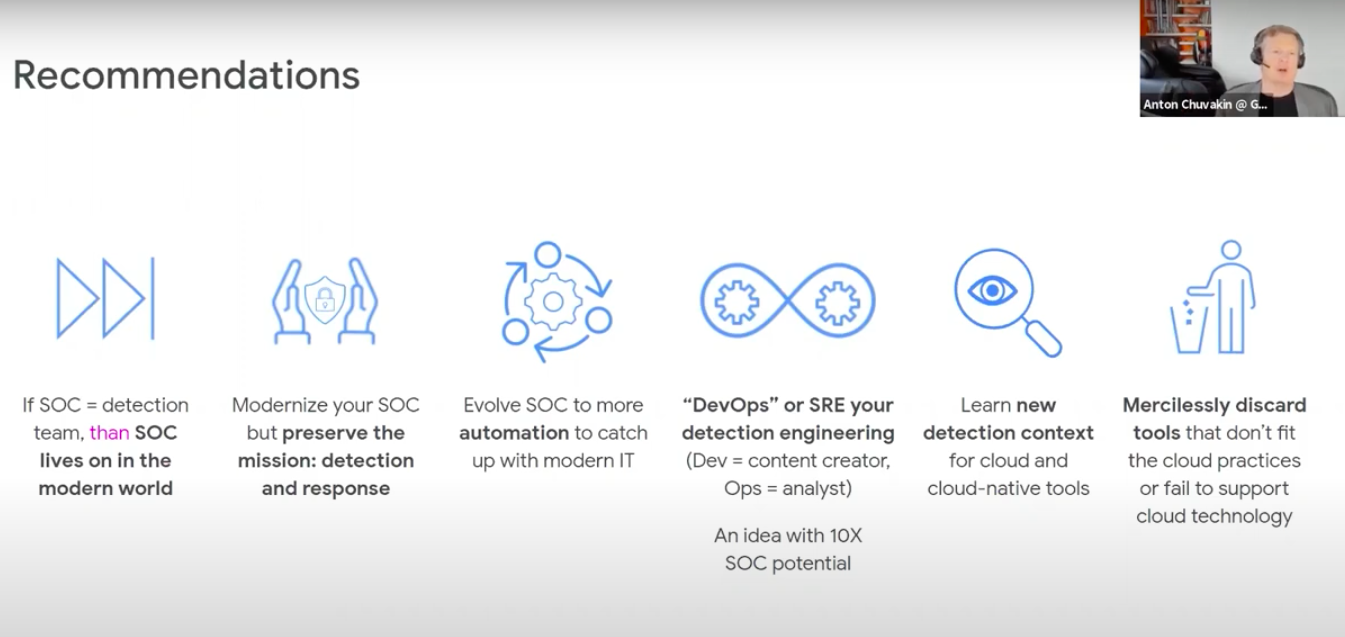
Recommendations
• If SOC = detection team, then SOC leaves on in the modern world
• Modernize your SOC but preserve the mission : detection and response
• Evolve SOC to more automation to catch up with modern IT
• “DevOps” or SRE your detection engineering (Dev = content creator, Ops = analyst). An idea with 10X SOC potential
• Learn new detection context for cloud and cloud-native tools
• Mercilessly discard tools that don’t fit the cloud practices or fail to support cloud technology
Resources
• Modernizing SOC .. Introducing automatic security operations
• New paper : Automatic Security Operations – 10X Transformation of the Security Operations Center
• SOC in a large, complex and evolving organization (ep26)
• The mysteries of detection engineering : Revealed (ep27)
• Kill SOC Toil, Do SOC Eng
• A SOC Tried to detect threats in the cloud .. you won’t believe what happened next
• Role of context in threat detection


Comments