The recent undocumented code in the ESP32 microchip, made by Chinese manufacturer Espressif Systems, is used in over 1 billion devices and could represent a cybersecurity risk. Its reveal by security researchers has kicked off an interesting discussi
vulnerability (24)
For over a decade, we warned the healthcare industry this was coming. They ignored us. Their sole focus was HIPAA compliance — checking regulatory boxes rather than securing critical systems. We told them that system and service availability attacks
Microsoft has stumbled yet again. Its Recall feature — intended to enhance user experience by periodically capturing screenshots — has become a glaring example of how well-intentioned technology can undermine security and privacy.
Does this sound fami
A “Perfect” 10 vulnerability score is not what users of Cisco Ultra-Reliable Wireless Backhaul (URWB) systems were expecting. The recently discovered cybersecurity vulnerability CVE-2024–20418 is remote, easy, and gives full Admin rights to the devi
I had a great discussion on the SECURITYbreak podcast talking about security vulnerability research impacting Apple vision pro VR headsets, MasterCard’s acquisition of threat intelligence vendor Recorded Future, and some horrific aspects of cybercrim
When cybersecurity researchers break the law, destroy their reputation, and make the bug-bounty research community look bad.
TL:DR Researchers found a vulnerability in a cryptocurrency exchange. They notified the company, but then exploited the bug to
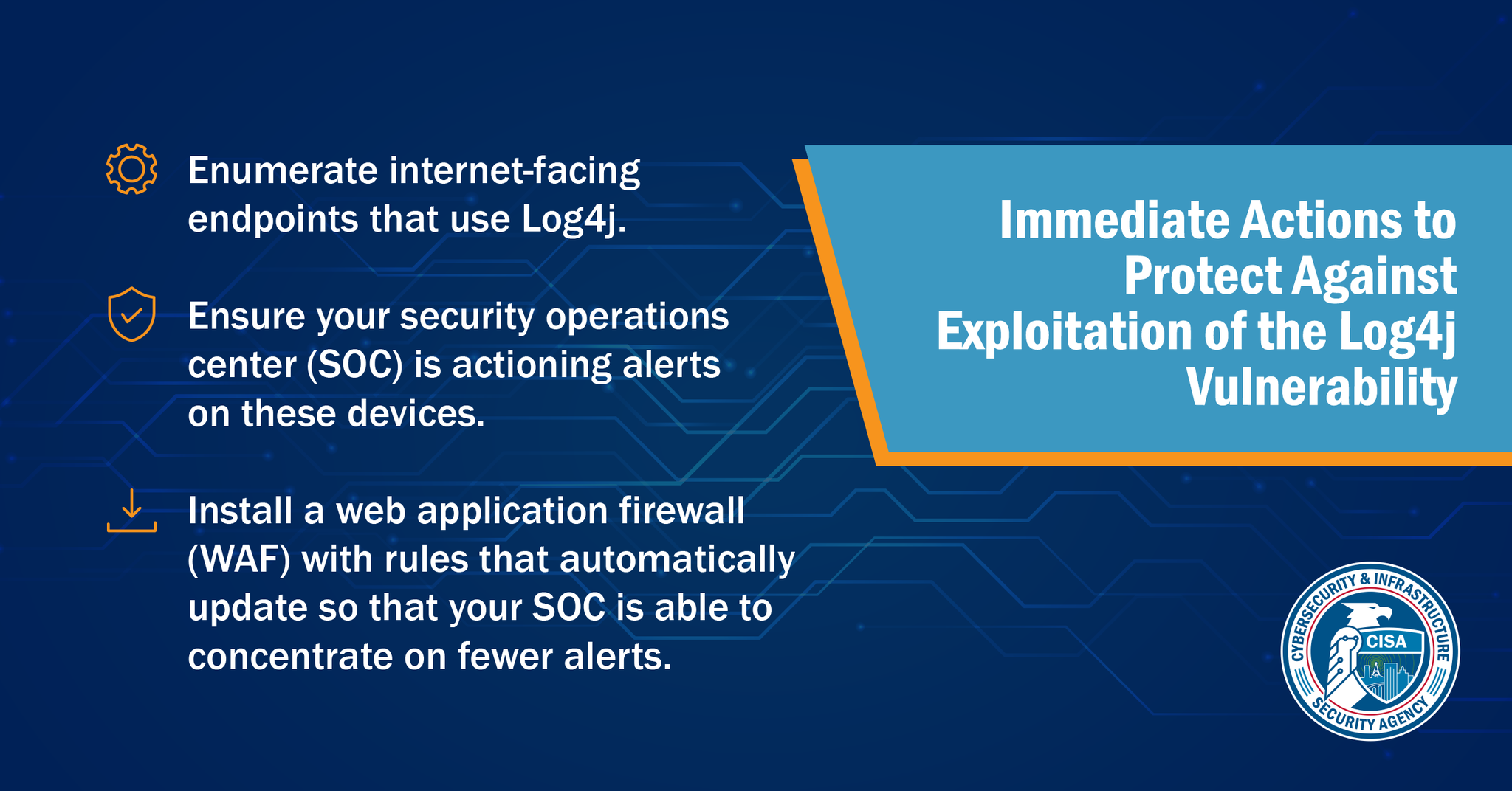
We're talking about the latest Java-based vulnerability CVE-2021-44228. Recently, a critical Zero-day vulnerability has been found in log4j which permits Remote Code Execution (RCE) allowing the attackers to get remote access. The Vulnerability got
 Recently, we were pentesting a Data mining and Analytics company. The amount of data that they talked about is phenomenal and they are planning to move to Big Data. They invited me to write a blog on state of the art, Big Data security concerns and c
Recently, we were pentesting a Data mining and Analytics company. The amount of data that they talked about is phenomenal and they are planning to move to Big Data. They invited me to write a blog on state of the art, Big Data security concerns and c
Our editorial team has handpicked some great talks from Black Hat Conference - one of the largest IT Security Conference in the world.
Black Hat - built by and for the global InfoSec community - returns to Las Vegas for its 19th year. This six day e
Overview
With the increasing need of Bluetooth Low Energy (BLE) IoT security, comes the part of vulnerability management in these networks. Unlike the IP security, BLE security framework is not yet mature. The newer version of BLE have enhanced the s
Many new devices are trying to fit into our life seamlessly. As a result, there’s a quest for a “universal access methods” for all devices. Voice activation seems to be a natural candidate for the task and many implementations for it surfaced in rece
Background:
It has been suggested that any new development will include less than 1% original code. If this isn’t presently true, it will likely be as time progresses.
With any security program, the goal is to identify the vulnerabilities, the relate
New CPU Vulnerabilities Discovered
RIDL/ZombieLoad and L1DES/CacheOut are just the latest variants of vulnerabilities discovered in Intel CPU’s that target Micro-architectural Data Sampling (MDS) weaknesses. Discovered over 7 months ago, researchers r
Bugcrowd has released some interesting survey data that provides insights into the white-hat vulnerability researcher community.
Of note, most researchers were male (94%) and make less than $25k per year finding vulnerabilities. A vast majority were m
Intel has released patches for several security vulnerabilities in their Active Management Technology (AMT) and Intel Standard Manageability (ISM) platforms. One of them was a critical flaw in AMT that allowed remote privilege escalation CVE-2020-8
The first warning sign was “hackproof” in the 360Lock marketing materials. As it turns out, with no surprise to any security professional, the NFC and Bluetooth enabled padlock proved to be anything but secure.
Recent verified reports highlight exploitable vulnerabilities in Apple’s security chip that cannot be patched! The announcement adds to the growing concerns and shifting perceptions about hardware security.
Hardware-based security has pros and cons.
The U.S. National Security Agency knows which vulnerabilities China backed hackers are exploiting the most to gain access to sensitive data.
The Chinese state-sponsored information gathering engine is a vacuum when it comes to acquiring information fr
A group of security vulnerability researchers, after many months of work, were able to figure out the update process and secret key used to decrypt Intel microcode updates for the Goldmont architecture product lines.
This is an important finding as it
CISO Platform
A global community of 5K+ Senior IT Security executives and 40K+ subscribers with the vision of meaningful collaboration, knowledge, and intelligence sharing to fight the growing cyber security threats.
Join CISO Community Share Your Knowledge (Post A Blog)
City Round Table Meetup - Mumbai, Bangalore, Delhi, Chennai, Pune, Kolkata
- Description: CISO Playbook Round Table Overview :
Our round tables are designed to bring together top CISOs and IT leaders in intimate, focused sessions. These closed-door discussions will provide a platform to explore key security challenges and solutions. These sessions aim to create a focused, closed-door environment where 08-10 CISOs will dive deeply into the practicalities of implementing specific technologies.- Technology Implementation: From…
- Created by: Biswajit Banerjee
- Tags: ciso, playbook, round table
CISO Cocktail Reception At RSAConference USA, San Francisco 2025 !
- Description:
We are excited to invite you to the CISO Cocktail Reception if you are there at the RSA Conference USA, San Francisco 2025. It will be hosted aboard a private yacht, so that our CISO's can enjoy the beautiful San Francisco skyline while cruising the Bay Area! This event is organized by EC-Council with CISOPlatform and FireCompass as proud community partners.
Yacht Party…
- Created by: Biswajit Banerjee
- Tags: ciso, usa, san francisco, rsaconference 2025
Round Table Dubai 2025 | GISEC
- Description: CISO Playbook Round Table Overview :
Our round tables are designed to bring together top CISOs and IT leaders in intimate, focused sessions. These closed-door discussions will provide a platform to explore key security challenges and solutions. These sessions aim to create a focused, closed-door environment where 08-10 CISOs will dive deeply into the practicalities of implementing specific technologies.- Technology…
- Created by: Biswajit Banerjee
CISO Platform: CISO 100 Awards & Future CISO Awards | In association with EC Council
- Description:
Nominate for the CISOPlatform CISO 100 Awards & Future CISO Awards - Recognizing Cybersecurity Leaders. Recommend someone you know deserving of this prestigious accolade....Nominate your colleague, mentor, someone you admire or yourself !
For more details: Click Here…
- Created by: Biswajit Banerjee