Ransomware is a growing scourge. Is it possible to eradicate this entire class of attacks? I think it is but in today’s Cybersecurity Insights interview I have a lively debate with Malcolm Harkins on criminalizing ransomware payments and different ap
All Posts (2220)
Technology can be mesmerizing. We are all lured by the seemingly endlessly tantalizing stream of emerging technologies that promise to connect and enrich our lives. But there is a potential dark side. For every great innovative benefit, there are acc
Firmware is the little-talked-about component of every digital device and computer system, that possesses tremendous control, and is now being targeted by cyber attackers. In today’s Cybersecurity Insights podcast, I am talking with Scott Scheferma
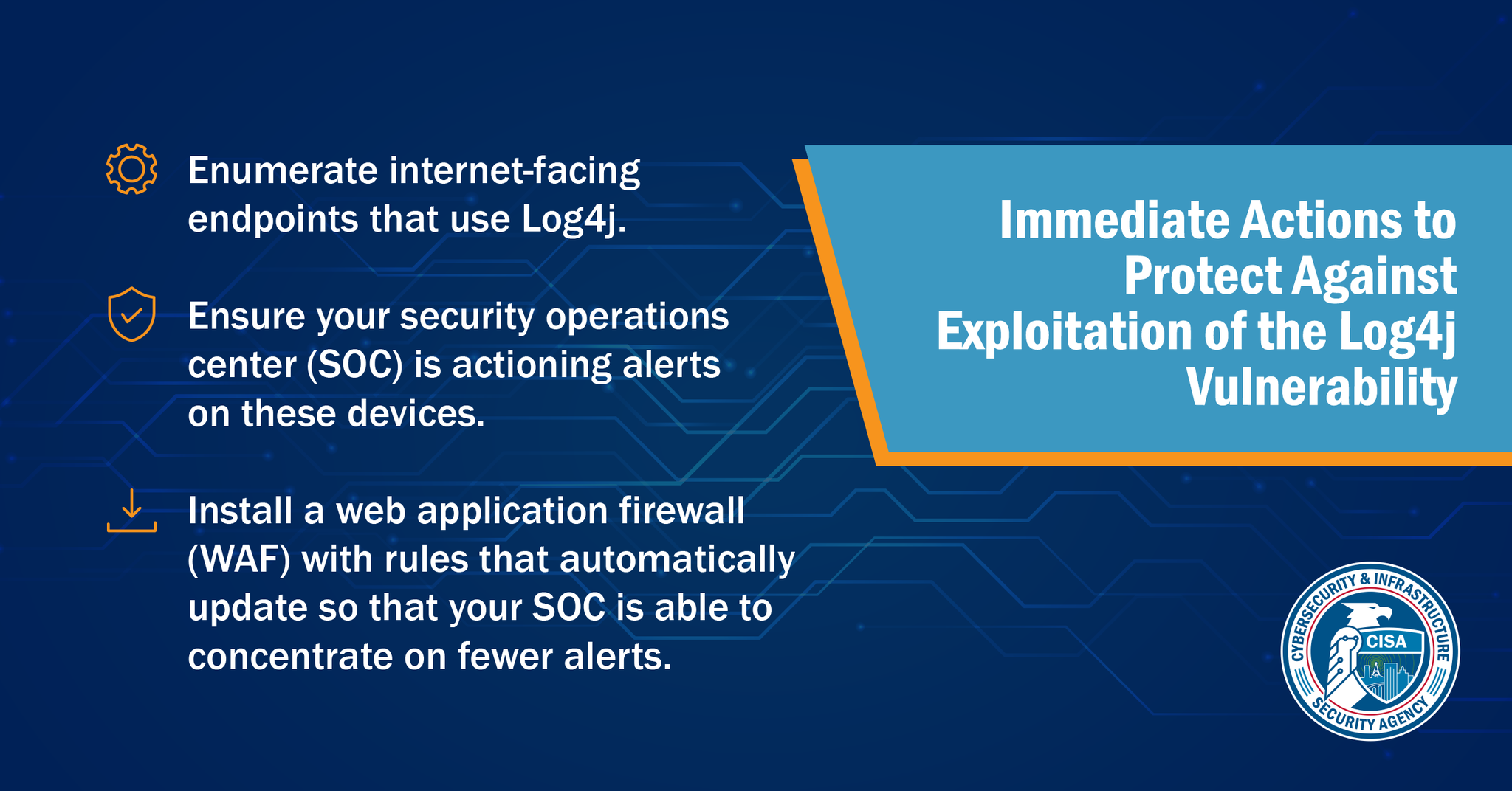
We're talking about the latest Java-based vulnerability CVE-2021-44228. Recently, a critical Zero-day vulnerability has been found in log4j which permits Remote Code Execution (RCE) allowing the attackers to get remote access. The Vulnerability got
New Fixes Added for CVE-2021-45046, CVE-2021-45105
Background on Apache log4j 2
Apache log4j 2 is an open source Java-based logging framework, which is leveraged within numerous Java applications around the world. Compared with the original log4j 1.X r
CISO Contributors
- Rajiv Nandwani (IT Security & physical security continuity senior manager, BCG)
- Vijay Kumar Verma (SVP & Head Cyber Security Engineering, Jio Platforms)
- Vikas kapoor (Vice President, Cyber Security, VOIS)
Panel Discussion (Rec
In this talk it present never before seen data on on the first three quarters of 2021. The cybersecurity industry is booming with record levels of funding, growing attacks, and massive hiring. At the same time, some companies are failing to thrive.
Our editorial team has handpicked the best talks at Discussion Summit - a small community summit where we aim to find out the problems and solutions currently faced in the cyber security industry. This talks is on 'Iranian Nationwide Terror And Intel
As we continue to move forward in the Industry 4.0 era of greater connectivity between the physical and digital, the promise and development of smart cities become a more likely vision. Keeping a smart city secure is a challenge as the urban safety e
Topic Brief
We already talked about developing a modern security operations center or a SOC and some of you were left with questions how do you actually journey ? how do you travel to this modern SOC ? It's easy to discuss what the modern SOC should
AI tech is a powerful tool. The original photo (left) was cleaned-up with an AI deep learning algorithm (Image source: from Murilo Gustineli) and restoring tremendous clarity.
The AI researchers outline their progress in their white paper Towards Real
Keynotes From World-Renowned Industry Experts (Best Of The World) :
- "The state of security markets and changing buying priorities" by Maria Kussmaul - Head Security, Investment Banking | Wharton School
- "Q3 2021 Changes To The Entire IT Secur
I recently presented to a small group on why cybersecurity is becoming more difficult over time, despite all the money and effort that is being applied. Sharing a replay of the presentation where I discuss cybersecurity history, root causes, shifting
I like the concept of ‘banning’ the sale of offensive cyber weapons to potential adversaries, but what defines technology as offensive versus defensive?
Israel just announced it will ban the sales of hacking and surveillance tools to 65 countries: htt
The cybersecurity industry had challenges with bringing in new blood and facilitating the career growth. Misinformation has unfortunately played a part in making various roles appear unattainable, when we should be doing the opposite. We should be
A new bill has been proposed to address Ransomware. Congressman Patrick McHenry recently introduced the Ransomware and Financial Stability Act of 2021.
Good Direction, but Falls Short
I believe it is the right direction for undermining ransomware attac
Recently introduced Ransomware and Financial Stability Act (H.R.5936) is the right direction for undermining ransomware attacks, by disallowing payments, but it just does not go far enough. This proposal only benefits traditional financial institutio
CISO Platform
A global community of 5K+ Senior IT Security executives and 40K+ subscribers with the vision of meaningful collaboration, knowledge, and intelligence sharing to fight the growing cyber security threats.
Join CISO Community Share Your Knowledge (Post A Blog)