All Posts (2220)
Unified Threat Management (UTM) is an all in one security solution that integrates firewalls, anti-viruses, content filtering, spam filtering, VPN protection, anti-spyware and other security system you need to protect your network. It can perform man
Here is the list of top 5 vendors emerging Threat Hunting tools, but before that let us understand what threat hunting exactly refers to.
Threat Hunting?
- Threat hunting is a proactive approach to identifying adversaries rather than reactively waiti
- Network Forensics is related to the monitoring and analysis of network traffic for the purposes of information gathering, legal evidence collection also to detect and identify any intrusion. Network investigation deals with volatile and dynamic da
Enterprise mobility management ( EMM ) is a suite of products which allows you to safely enable the use of mobile devices in your organization. Employees today want to use their personal devices for checking corporate mails and access sensitive docum

- FireCompass, an AI based platform which helps you to discover & compare Cybersecurity products has just announced the names of Top CyberSecurity Startups 2017 (India).
- With the growing cyber attacks, the role of innovations in the cyber-security
Security Maturity Score By Industry :
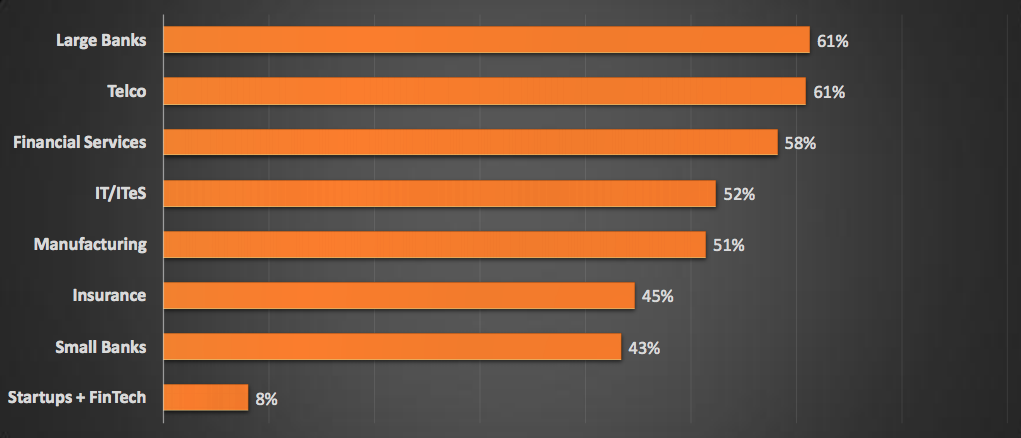
Identification Capabilities By Industry :
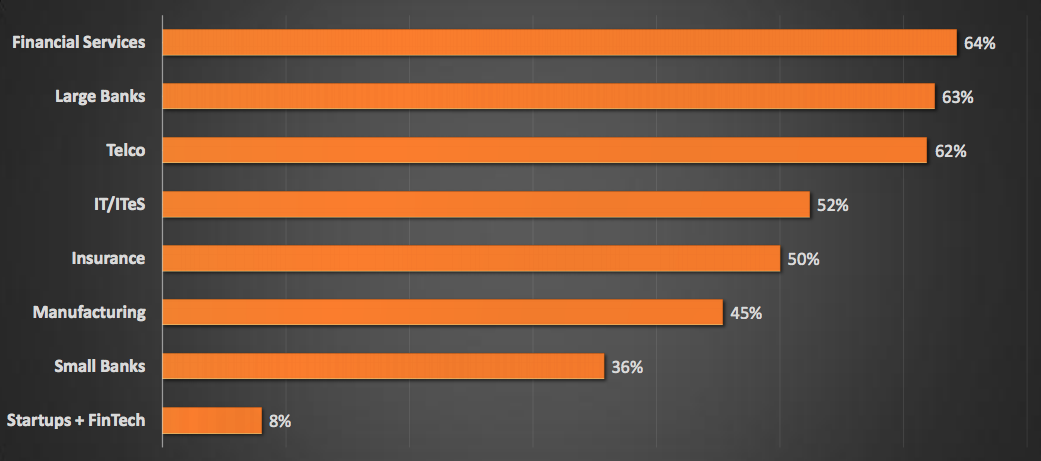
Prevention Capabilities By Industry :
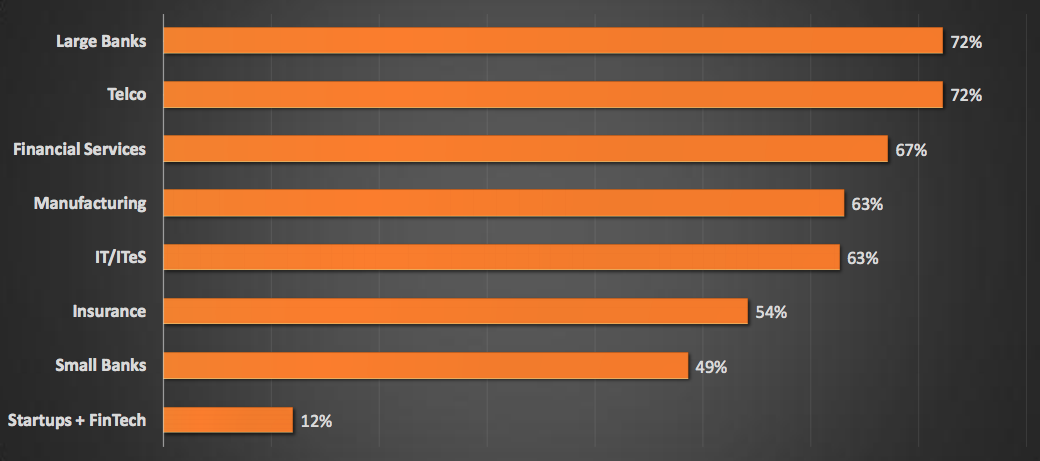
Detection Capabilities By Industry :
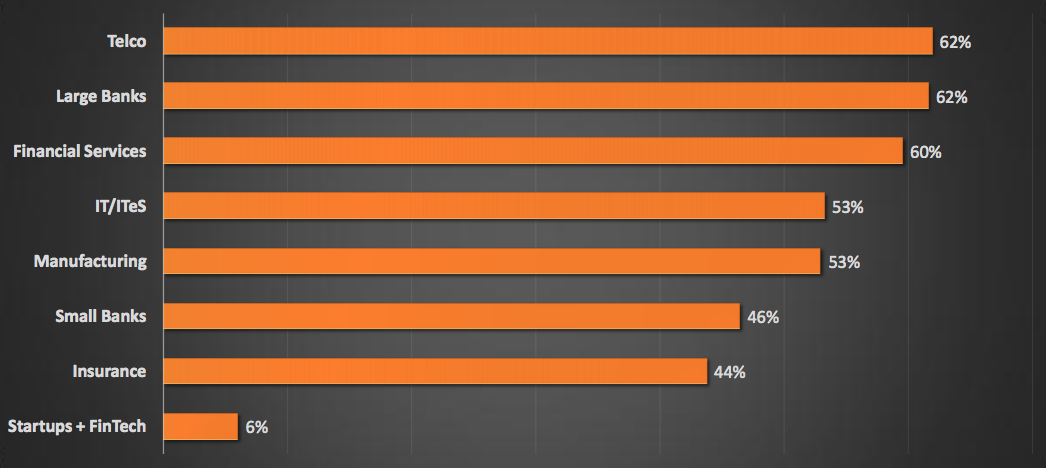
Response Capabilities By Industry :
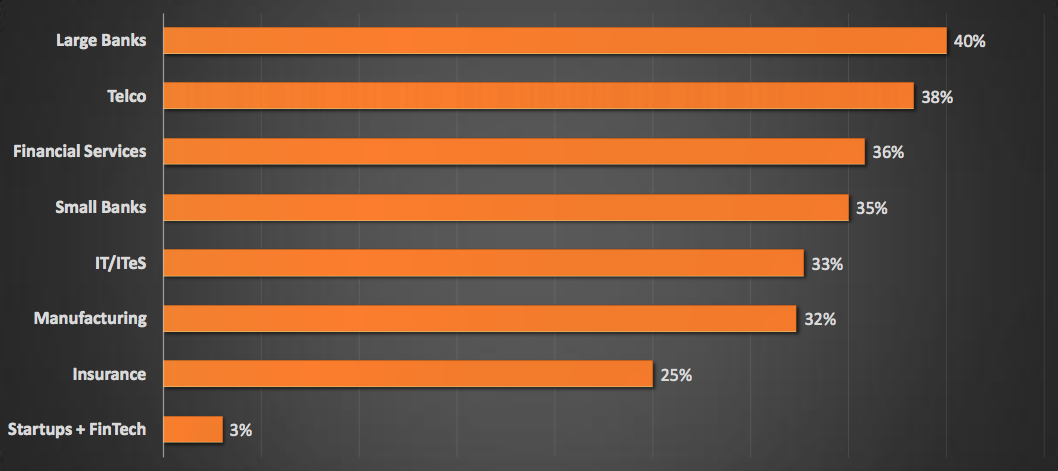
Key Findings :
- Large Indian
Vulnerability assessment is a process that defines, identifies, and classifies the security holes in a computer, network, or communications infrastructure. In addition, vulnerability analysis can forecast the effectiveness of proposed countermeasures
It is very important to properly define the right Information Security Metrics for an organization to estimate the security structure and to communicate it efficiently to the Board level executives.There is a growing interest from the Board and th
We are happy to share that FireCompass has been selected as a winner of NASSCOM’s 2017 Emerge 50 award. At FireCompass our vision is to transform the way enterprises make security strategy and buying decisions.
RSA conference is one of the leading security conference worldwide. It creates tremendous opportunity for vendors, users and practitioners to innovate, educate and discuss around the current security landscape.
Web Security Gateway Vendors provid
RSA conference is one of the leading security conference worldwide. It creates a tremendous opportunity for vendors, users and practitioners to innovate, educate and discuss around the current security landscape. This blog enlists the top End point
RSA conference is one of the leading security conference worldwide. It creates tremendous opportunity for vendors, users and practitioners to innovate, educate and discuss around the current security landscape.
Identity and Access Management is the
- We are here, once again, with our list of Top 20 Emerging IT Security Vendors from 500+ vendors attending RSAC 2018, April 16 to 20 in San Francisco.
- BTW, We have also created a RSAC 1-Minute Itinerary tool for the ease of attendees, through which y
An emerging technology, Endpoint Detection and Response (EDR) constitutes a set of tools and solutions that enterprises use to detect, investigate and mitigate suspicious activities on hosts and endpoints. The term was originally called as Endpoint T
Distributed denial-of-service (DDoS) attack is one in which a multiple sources attack a single target causing denial of service for legitimate users of the targeted system. The flood of incoming traffic totally overwhelms the system, hence denying se
Distributed denial-of-service (DDoS) attack is one in which a multiple sources attack a single target causing denial of service for legitimate users of the targeted system. The flood of incoming traffic totally overwhelms the system, hence denying se
Distributed denial-of-service (DDoS) attack is one in which a multiple sources attack a single target causing denial of service for legitimate users of the targeted system. The flood of incoming traffic totally overwhelms the system, hence denying se
CISO Platform in association with FireCompass launches India Security Buying Priority Report (2018). This is the annual survey in which 395+ Companies have participated in the enterprise segment, varying over different verticals and regions. The key
CISO Platform
A global community of 5K+ Senior IT Security executives and 40K+ subscribers with the vision of meaningful collaboration, knowledge, and intelligence sharing to fight the growing cyber security threats.
Join CISO Community Share Your Knowledge (Post A Blog)

